Establishing security is one of the most important and, of course, most challenging issues that developers need to implement. Website security is done in many different ways, but one of the most consistent and, of course, most important parts of security is building authentication and authentication capabilities.
One of the main ways to prevent this is by implementing robust authentication and authentication. As a result, these two are very important issues that you must consider when developing applications.
In this exclusive article from the Rocket website, we will compare these two cases and understand what each one is. Learning this is vital for back-end developers.
Authentication vs. validation
In this section, we want to make their concepts clearer for you by creating a boundary between the two.
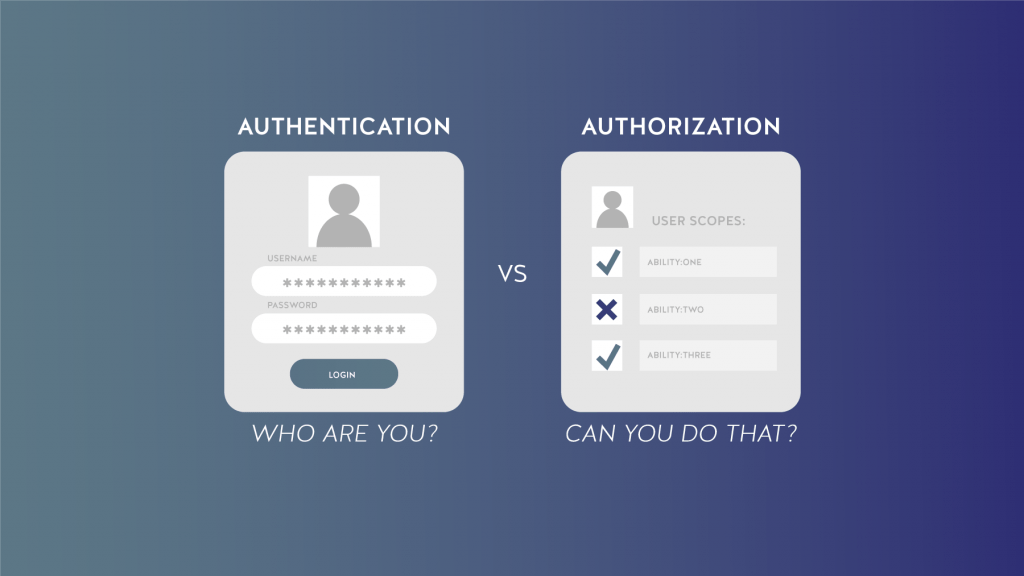
Authentication: Authentication is a process in which the person’s identity who intends to log in is checked. If confirmed as to whether this person is the person who can log in, enter the application.
For example, if a person intends to log in to the website using the login form or login, his username and password should be checked normally, and if it is correct, he should be directed to the admin panel.
Validation: Validation is the process of determining who has access to what data. Validation is the post-authentication stage.
For example, the person who entered the admin panel in the previous example must have specific access to different sections. For example, if this person is the main webmaster, he will delete the entire website. But if he is an author, he should only have access to the articles section.
There are many examples of this. These two issues have good implentation in content management systems. For example, in WordPress, to manage the validation section, you can specify the level of access of each user to different sections of the website in the admin panel through the user’s section.
Web frameworks such as Laravel and Django also have ready-made capabilities for managing these sections. As a result, if you are a developer of these two frameworks, you can easily implement authentication and authentication capabilities.
Another example: Imagine you are planning a trip by plane. When you arrive at the airport, someone will ask you for a plane ticket in the first step. If you have a plane ticket, you can get on the plane. This is the authentication step. Next, if you have special requests such as food and drink on the plane, the service provider should check whether your ticket is eligible for such services. This will be the validation step.
The differences
Authentication seeks to verify the individual’s identity, but authentication determines the level of access of the verified person to the various resources of the website.
Authentication uses methods such as a fixed and one-time password, biometric information (fingerprint, iris, etc.), and other items used to log in to verify the person’s identity. But validation is the next step after authentication, which the main programmer must code to implement and how.
The user observes the authentication steps and interacts directly with them.
Conventional methods for authentication
There are various methods of authentication, some of which are very common and some of which are clever methods that are very popular today. Let’s take a look at these methods:
Username and Password: The most common and basic way to manage authentication is to use a username and password. Surely you have encountered this type of authentication and encountered it to enter various sites.
I’m not a robot: With the spread of hacking to the website, another option has been added to the usual username and password. The user confirms his human identity after entering a username and password using a question in this method. One of the most common of these questions is the images that Google shows you and asks you to select images that show, for example, an engine. Bats usually do not have the ability to solve this problem, but humans can easily do it.
One-time password: Some websites require you to enter a code sent to your mobile phone or email as a one-time password. This is one of the safest ways to verify your identity.
Biometric information: This method is used in websites with very high data sensitivity. The user must use his fingerprint or iris to enter the website in this method. Because they are unique, it is almost impossible for other people to bypass them.
In most cases, authentication usually has a fixed part, such as username and password, and is used after other cases. So you can use these in combination and multiple times.
Conventional methods for validation
After you do the authentication steps, we will enter the validation phase. There are different methods for implementing this step, and in this section, we will look at two of these methods:
Role-Based Access Control
In this way, members of the organization will have access to information based on their roles. In an organization, for example, all regular employees may read documents but not be able to change them. On the other hand, the human resources manager will have the ability to have direct access to documents and even change them. This structure is one of the most common methods that you can see in the WordPress content management system.
Attribute-Based Access Control
In this method, accesses are provided based on the properties and characteristics that a user will have. For example, a user’s username could indicate what level of access they could receive. In this method, which may be more complicated to implement, it is necessary to control the user letters or other personal details. The most common feature used in this case is the individual’s national or organizational code.
In conclusion: Look for a solid strategy for authentication and authentication.
One of the most important security requirements of a website is its authentication and validation. Remember that this will be your front line against hacking and infiltration. As a result, it is better to consider a solid and integrated strategy for managing this sector.